Security Data Flow Diagram Flow Security Diagram Data Networ
Security data flowchart vector royalty Data flow diagram (dfd) software Process flow vs. data flow diagrams for threat modeling
Cyber Security Isometric Flowchart Royalty Free Vector Image | The Best
Data flow diagram Data flow diagram showing how data from various sources flows through Security network diagram model cloud diagrams government computer solution devices conceptdraw access example networks architecture cybersecurity solutions information models examples
Network security diagrams
Security flow chart test flowcharts flowchart testing structure diagrams validity proxy professional whenSecurity network diagram architecture firewall example computer diagrams cyber clipart model networks conceptdraw recommended microsoft access examples solution devices infrastructure 5 cornerstones to a successful cybersecurity programEnterprise password manager.
Create a data flow diagramMicrosoft graph security api data flow Flow webrtc aware modelingThe following data flow diagram template highlights data flows in a.

External security policy
Password manager data database manageengine security server flow diagram pro ssl between products reset pmp specifications remote enterprise transmission occurNetwork security model Security flowchartYour guide to fedramp diagrams.
[diagram] data flow diagram exam systemApplied sciences Network security flow diagramFlow security diagram data network slideshare upcoming.

Architecture cybersecurity enterprise iot cyber security diagram system software
Security event logging, why it is so important – aykira internet solutionsSecurity flow data cyber event logging diagram internet logs important why so together showing concerning events au putting Security apiFlow data diagrams process threat modeling diagram vs application dfd cloud engineering user owasp source response choose board.
Access control system flow chartData flow mapping template Flow data diagram security level dfd system visit yc examples networkData flow privacy.

Test security flowcharts
Data flow diagram in software engineering(pdf) solution-aware data flow diagrams for security threat modeling Flow chart for security system.Data flow diagram vs flowchart.
Data flow diagramData flow diagram of smart security framework Cyber security isometric flowchart royalty free vector imageFlow security chart documentation overview api diagram zendesk app diagrams example itunes amazon.

Data flow and security overview
Data flow diagram data security, png, 1506x1128px, diagram, areaIot & enterprise cybersecurity Flow dfd lucidchart logicalData security flowchart royalty free vector image.
Cyber security flow chartSecurity network diagram control devices diagrams computer networks access solution encryption secure model architecture conceptdraw example cloud software area examples Network security diagrams.


Data Flow Diagram Data Security, PNG, 1506x1128px, Diagram, Area

5 Cornerstones to a Successful Cybersecurity Program

Network Security Diagrams | Network Security Architecture Diagram
Data Flow Diagram vs Flowchart - What's the difference? | Miro

IoT & Enterprise Cybersecurity - Zymr
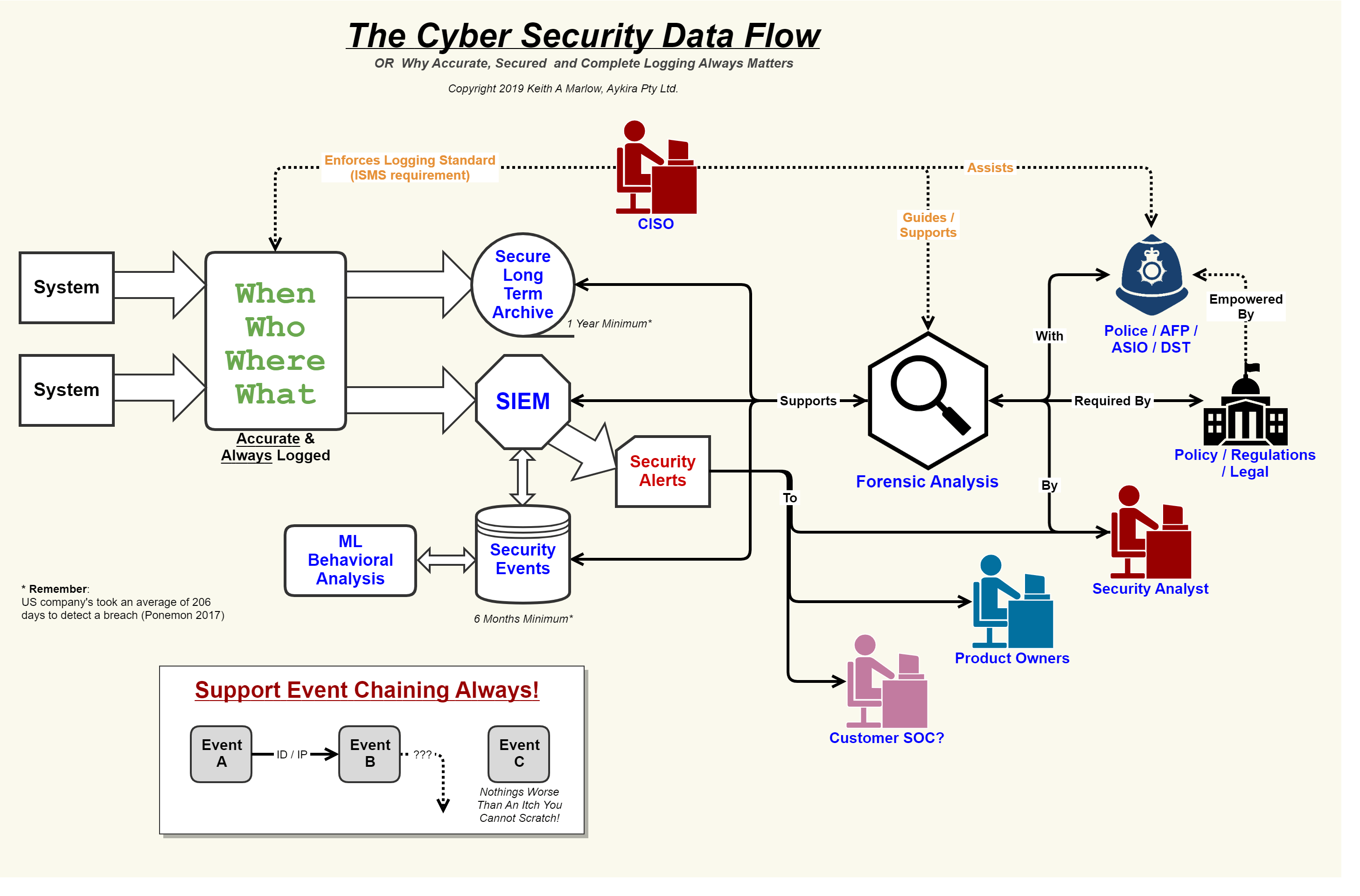
Security Event Logging, why it is so important – Aykira Internet Solutions

Cyber Security Isometric Flowchart Royalty Free Vector Image | The Best